Introduction
When first networking was used, it was limited to Military and Universities for Research and development purposes. Later when all networks merge together and formed Internet, user’s data use to travel through public transit network, where users are not scientists or computer science scholars. Their data can be highly sensitive as bank’s credentials, username and passwords, personal documents, online shopping or secret official documents.All security threats are intentional i.e. they occur only if intentionally triggered. Security threats can be divided into the below mentioned categories:
- Interruption:
Interruption is a security threat in which availability of resources is attacked. For example, a user is unable to access its web-server or the web-server is hijacked. - Privacy-breach:
In this threat, the privacy of a user is compromised. Someone, who is not the authorized person is accessing or intercepting data sent or received by the original authenticated user. - Integrity:
This type of threat includes any alteration or modification in the original context of communication. The attacker intercepts and receives the data sent by the Sender and the attacker then either modifies or generate false data and sends to the receiver. The receiver receive data assuming that it is being sent by the original Sender. - Authenticity:
When an attacker or security breacher, represents himself as if he is the authentic person and access resources or communicate with other authentic users.
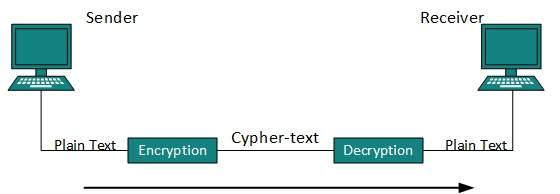
- Secret Key
- Public Key
- Message Digest
Secret Key Encryption
Both sender and receiver have one secret key. This secret key is used to encrypt the data at sender’s end. After encrypting the data, it is then sent on the public domain to the receiver. Because the receiver knows and has the Secret Key, the encrypted data packets can easily be decrypted.Example of secret key encryption is DES. In Secret Key encryption it is required to have a separate key for each host on the network making it difficult to manage.
Public Key Encryption
In this encryption system, every user has its own Secret Key and it is not in the shared domain. The secret key is never revealed on public domain. Along with secret key, every user has its own but public key. Public key is always made public and is used by Senders to encrypt the data. When the user receives the encrypted data, he can easily decrypt it by using its own Secret Key.Example of public key encryption is RSA.
Message Digest
In this method, the actual data is not sent instead a hash value is calculated and sent. The other end user, computes its own hash value and compares with the one just received. The both hash values matches, it is accepted otherwise rejected.Example of Message Digest is MD5 hashing. It is mostly used in authentication where user’s password is cross checked with the one saved at Server.
No comments:
Post a Comment